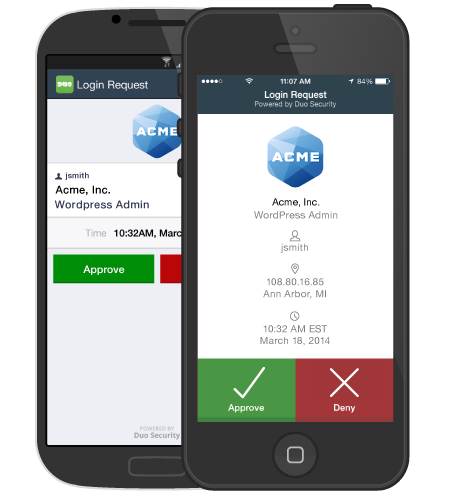
In today’s environment, when many employees are working remotely, it is important for organizations to identify users and verify the security of their devices before opening access to various corporate applications and services. The Duo Security solution can help.
Duo Security is a developer of authentication systems that Cisco officially acquired in 2018. Thus, Duo’s CEO and his team have joined the Cisco network technology and security business.
Duo Security Solutions verifies the identity of users and the status of their devices before giving them access to applications. This helps prevent cyber security breaches. Integrating Cisco systems with zero-confidence Duo authentication products helps Cisco customers easily and securely connect users to any application on any network device.
Why is Duo Security useful?
 We live in an era of access, and the cybersecurity industry is severely disrupted. Business-critical confidential data is now available to customers, partners, and employees who do not always use secure networks. And during the quarantine period, the probability of using such networks becomes even greater.
We live in an era of access, and the cybersecurity industry is severely disrupted. Business-critical confidential data is now available to customers, partners, and employees who do not always use secure networks. And during the quarantine period, the probability of using such networks becomes even greater.
Duo Security products help you connect and use digital features securely.
Duo Security is:
- Secure access.
The program will detect infections on third-party devices even before they are connected. This is an easy-to-use protection that allows you to do exactly what has real meaning.
- Verified users.
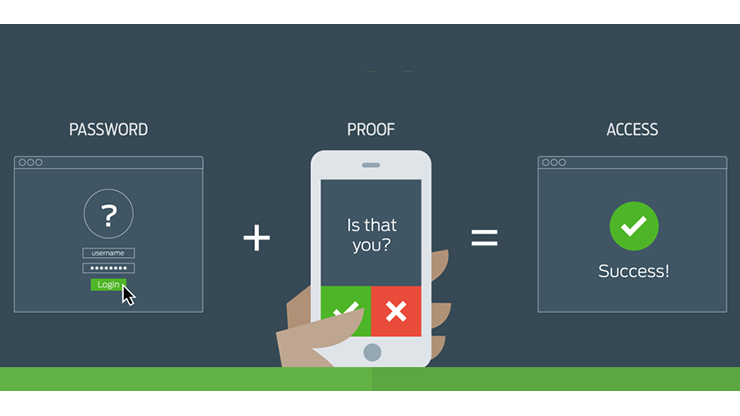
Two-factor authentication of all users will help determine the truth of their identity. Also, such authentication provides the opportunity to introduce the most stringent policies regarding the availability of data for each employee.
- Scan device.
Another feature of DUO protection is to check the user’s device for old software and missing security protocols.
- All applications and data are protected.
No matter where your data is located, in the cloud or on a physical server, it will always be protected by malicious influences.
- One authorization
Using Single sign-on (SSO) technology, logging in for each employee will be as simple as possible. Logging in to the system will be enough once to ensure constant access to any application of the enterprise.
- Ubiquitous access.
During remote work, when all employees use their own devices to access the applications of their organization, this function becomes more popular and useful. They can access data from anywhere.
Additional Duo features for administrator convenience and increased resource access protection:
- Custom Self Service
- Geographic Filters
- Deny access to anonymous networks
- Block or grant IP access
- Ability to set individual authentication requirements for users with the highest level of access.
- Control the level of protection of mobile devices on which the Duo Mobile application is installed, from viruses and the possibility of hacking.
Duo Security pricing depends on the number of features available. Despite the fact that Duo tariffs cannot be called cheap, in comparison with their large competitors (RSA, Vasco, Gemalto, etc.), their pricing policy is quite acceptable and consistent with its functionality. Learn more about this solution from our specialists.



 ESET has developed a special solution for protecting confidential data, as well as providing control over the actions of employees that affect their performance of their duties – DLP Safetica.
ESET has developed a special solution for protecting confidential data, as well as providing control over the actions of employees that affect their performance of their duties – DLP Safetica.

 The Romanian company Bitdefender has developed one of the world’s most popular antiviruses, the functionality of which has a complete set of tools to prevent any virus attacks. Such an antivirus has a built-in firewall, intispam and antiphishing functions that block suspicious sites; multi-level protection of personal data and even webcam protection.
The Romanian company Bitdefender has developed one of the world’s most popular antiviruses, the functionality of which has a complete set of tools to prevent any virus attacks. Such an antivirus has a built-in firewall, intispam and antiphishing functions that block suspicious sites; multi-level protection of personal data and even webcam protection. Of the advantages of this software can be identified:
Of the advantages of this software can be identified: This product of the Czech company Avast Software back in 2017 became one of the most popular, surpassing all its competitors in many criteria and qualities. Such software can be bought at an affordable price and get reliable protection, practically without loading the processor.
This product of the Czech company Avast Software back in 2017 became one of the most popular, surpassing all its competitors in many criteria and qualities. Such software can be bought at an affordable price and get reliable protection, practically without loading the processor.
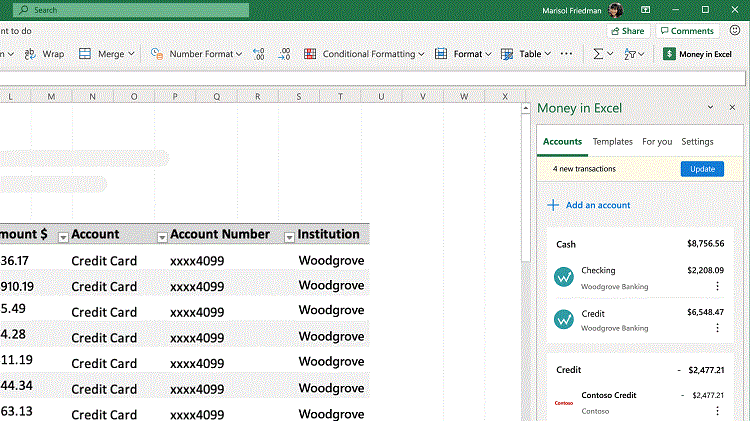 This function should greatly simplify financial management. It allows you to link bank accounts and credit card data so that Excel collects important data on income and expenses in a table and provides personalized financial analytics.
This function should greatly simplify financial management. It allows you to link bank accounts and credit card data so that Excel collects important data on income and expenses in a table and provides personalized financial analytics. Updated Teams will allow you to create groups to plan trips, create a schedule of events. Also, it will be possible to unite in group chats, conduct video calls, together make lists of tasks and set tasks for individuals. In addition, Teams will add tools for storing important information.
Updated Teams will allow you to create groups to plan trips, create a schedule of events. Also, it will be possible to unite in group chats, conduct video calls, together make lists of tasks and set tasks for individuals. In addition, Teams will add tools for storing important information.
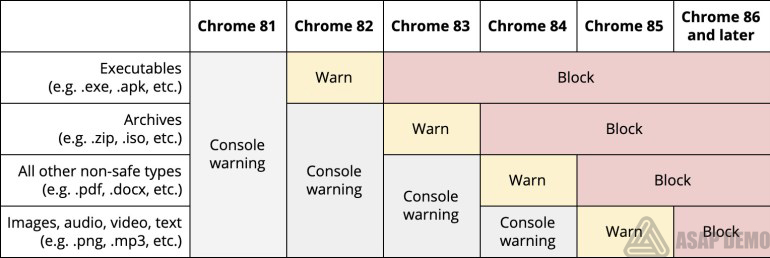 In the current version of Chrome 80, automatic updating of “mixed” audio and video content is enabled when possible. Also, corresponding notifications about mixed content appeared on the page for users – they will be displayed in the Omnibox line.
In the current version of Chrome 80, automatic updating of “mixed” audio and video content is enabled when possible. Also, corresponding notifications about mixed content appeared on the page for users – they will be displayed in the Omnibox line.